We're happy to announce the release of BusKill v0.7.0!
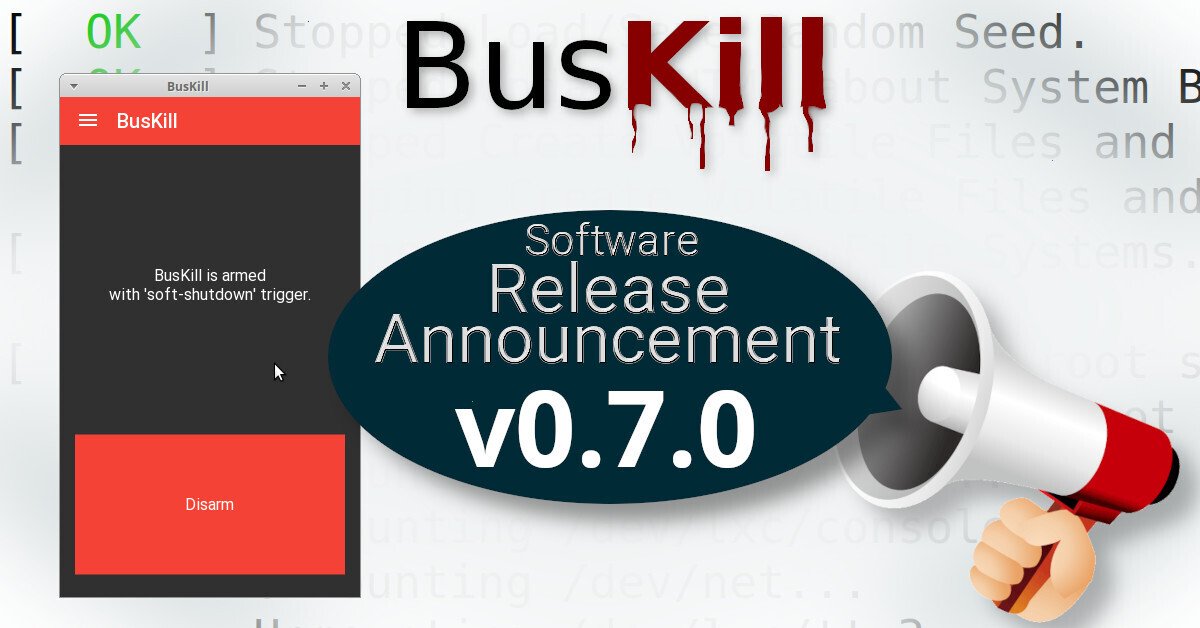
Most importantly, this release allows you to arm the BusKill GUI app such that it shuts-down your computer when the BusKill cable's connection to the computer is severed.
What is BusKill?
BusKill is a laptop kill-cord. It's a USB cable with a magnetic breakaway that you attach to your body and connect to your computer.
If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys -- thus keeping your encrypted data safe from thieves that steal your device.
Upgrading
You can upgrade your BusKill app to the latest version either by
- Clicking "Update"
in the app or
- Downloading it from GitHub
Changes
This update includes many bug fixes and new features, including:
- Adds support for 'soft-shutdown' trigger to GUI
- Adds a new
buskill.ini config file
- Adds a new "Settings" screen in GUI
- Merges kivy & buskill config files into one standardized location
- Fixes in-app updates on MacOS
- Fixes lockscreen trigger on Linux Mint Cinnamon
- Fixes background blue/red disarm/arm color to propagate to all screens
- Fixes
--run-trigger to be executed inside usb_handler child process and communicate to root_child through the parent process
You can find our changelog here:
Documentation Improvements
We've also made many improvements to our documentation
- Updated the Software User Guide to include how to arm the BusKill app with the
soft-shutdown trigger in the GUI
- Added a manpage
- Better documentation on how to build your own USB-C BusKill Cable
- Better documentation on how to test the buskill app
- Fixes in Release Workflow
- Added some additional related projects to our documentation
Soft-Shutdown Trigger
This release now allows you to choose between either [a] locking your screen or [b] shutting down your computer when you arm the BusKill app from the GUI. By default, the BusKill app will trigger the lockscreen. To choose the 'soft-shutdown' trigger, open the navigation drawer, go to the Settings Screen, click Trigger, and change the selected trigger from lock-screen to soft-shutdown. For more information, see our Software GUI User Guide.
BusKill Now in Debian!
We're also happy to announce that, with the release of Debian 12, it's now possible to install BusKill in Debian with Apt!
sudo apt-get install buskill
Testers Needed!
We do our best to test the BusKill app on Linux, Windows, and MacOS. But unfortunately it's possible that our app doesn't fully function on all versions, distributions, and flavours of these three platforms.
We could really use your help testing the BusKill app, especially if you have access to a system that's not (yet) listed in our Supported Platforms.
And in this release, we specifically would like you to help us test the new soft shutdown feature. Please let us know if it does or does not work for you.
Please contact us if you'd like to help test the BusKill app :)



