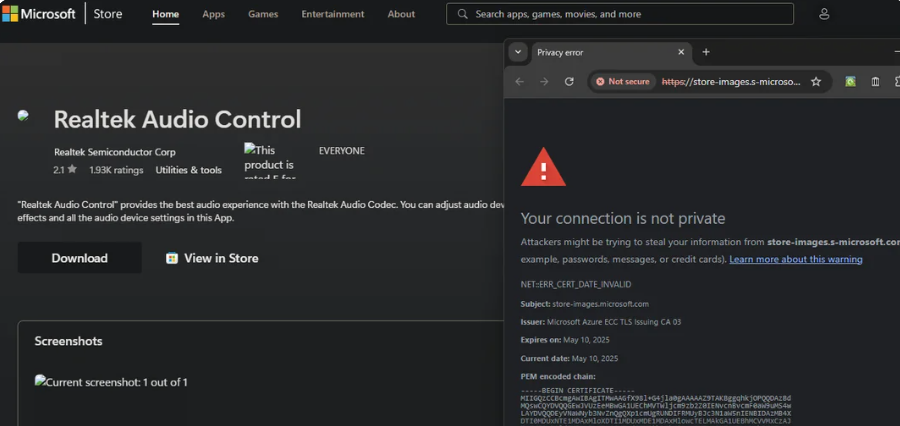
With LetsEncrypt phasing out expiry reminder emails, I’m expecting to see this shit more and more often soon
iiiiiiitttttttttttt
you know the computer thing is it plugged in?
A community for memes and posts about tech and IT related rage.
Why would they phase that out?
Because it's not very useful, very replacable, requires them to keep email addresses, and it's costing them extra resources for the free service they provide.
Because no one should rely on that, they recommend to fully automate renewal with a script or some other programs.
What if there script is broken or not running properly? I would still want to be informed before I get a complaint from an user.
Then set-up a fucking Monitoring service. Not their problem
Manjaro: "First time?"
Must be a lot of vibe in the code over there these days.
30% appearently.
That's true I read that hahah
How do you all manage this ?
They manually create certs at my job then manually move them other to a network drive and then a gpo? policy installs those certs to AD users.
I found a way to automate this process (but company didn't care)
But I'm not an IT person, what's the best approach for doing this on promises?
edit: I like the responses but I was hoping for something that wouldn't use 3rd party products. What if hypothetically the certificates were self signed and you wouldn't need a 3rd party CA?
Another thing is: is using 3rd party CAs really the most common way ?
Luckily Let's Encrypt made automation more popular. Every new domain of mine gets a cert that is renewed automatically. I don't have to worry at all about it.
How do you manage automatic renewal?
A cronjob calling Let's Encrypt's tool. I think it's called certbot.
I use caddy as reverse proxy and you have to do... Literally nothing. Point the domain at your server and write in the Caddyfile
my.domain { reverse_proxy myservice:3000 }
It also supports wildcard certificates for many domain services
For my personal setup at home: Traefik with LE
I think at work my technical lead buys multi-year certs and manually imports them.
Some clients of us use LE in some combination with another software.
I use a cronjob with cerbot to renew
I also have Uptime Kuma setup to alert if certificates are getting close to expiration
They got that vibe
Yoink
The address is store-images (dot) s-microsoft (dot) com. Is that Microsoft tld? If so, it sure looks like a phishy one to me...
Edit: whois states is a Microsoft-registered domain. Wow. That's..... wow
Considering its the url used in the microsoft store, I'd assume it is.
The name servers are also azure urls.
That doesn't mean you don't have a browser hijacker malware, though, so I always check destination urls.
IT? More like UT; Urrr Technology