this post was submitted on 11 Feb 2025
1347 points (98.6% liked)
Programmer Humor
23507 readers
1404 users here now
Welcome to Programmer Humor!
This is a place where you can post jokes, memes, humor, etc. related to programming!
For sharing awful code theres also Programming Horror.
Rules
- Keep content in english
- No advertisements
- Posts must be related to programming or programmer topics
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
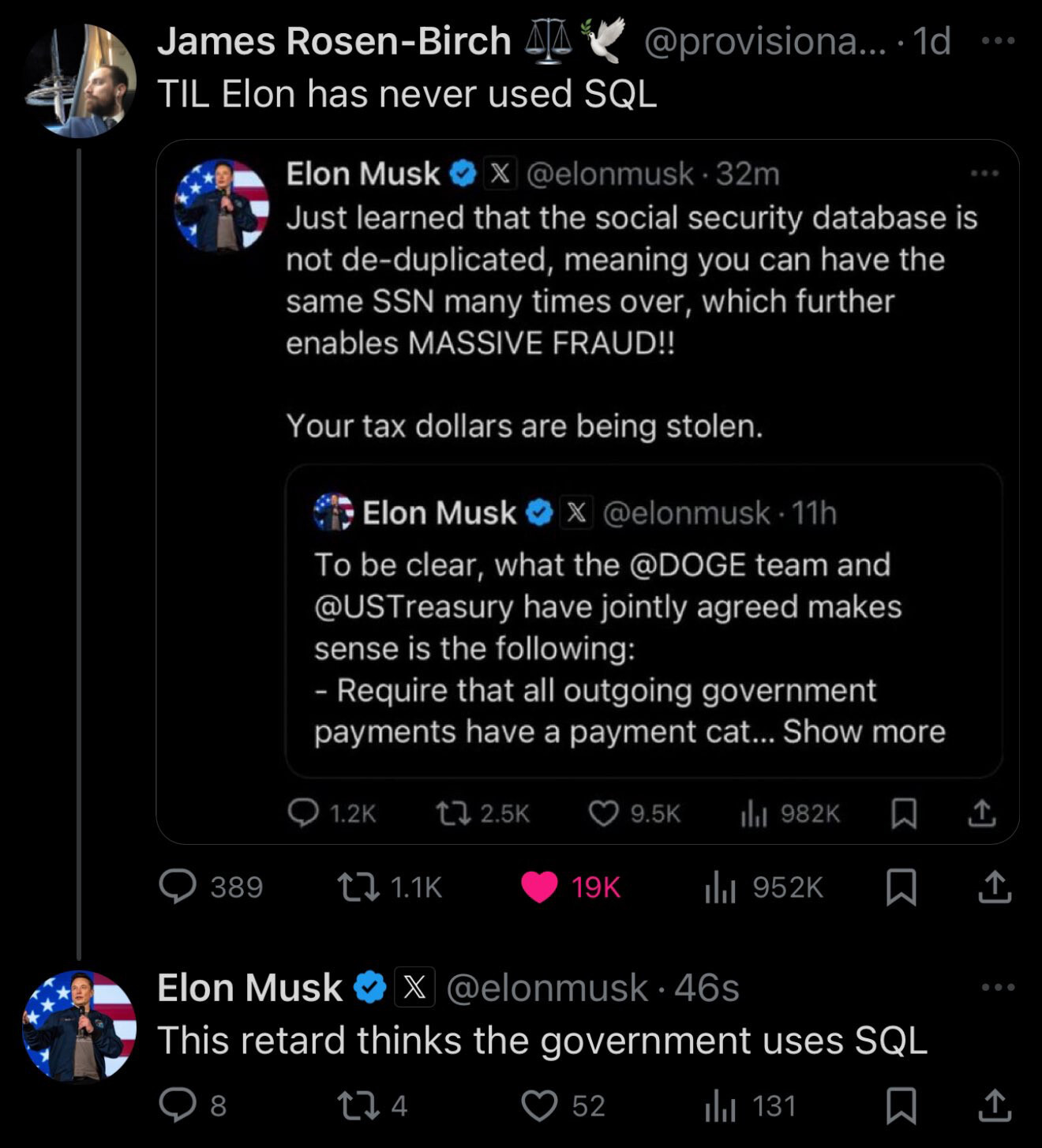
No. You can have control over specific parameters of an SQL query though. Look up insecure direct object reference vulnerabilities.
Consider a website that uses the following URL to access the customer account page, by retrieving information from the back-end database:
https://insecure-website.com/customer_account?customer_number=132355Here, the customer number is used directly as a record index in queries that are performed on the back-end database. If no other controls are in place, an attacker can simply modify the customer_number value, bypassing access controls to view the records of other customers.