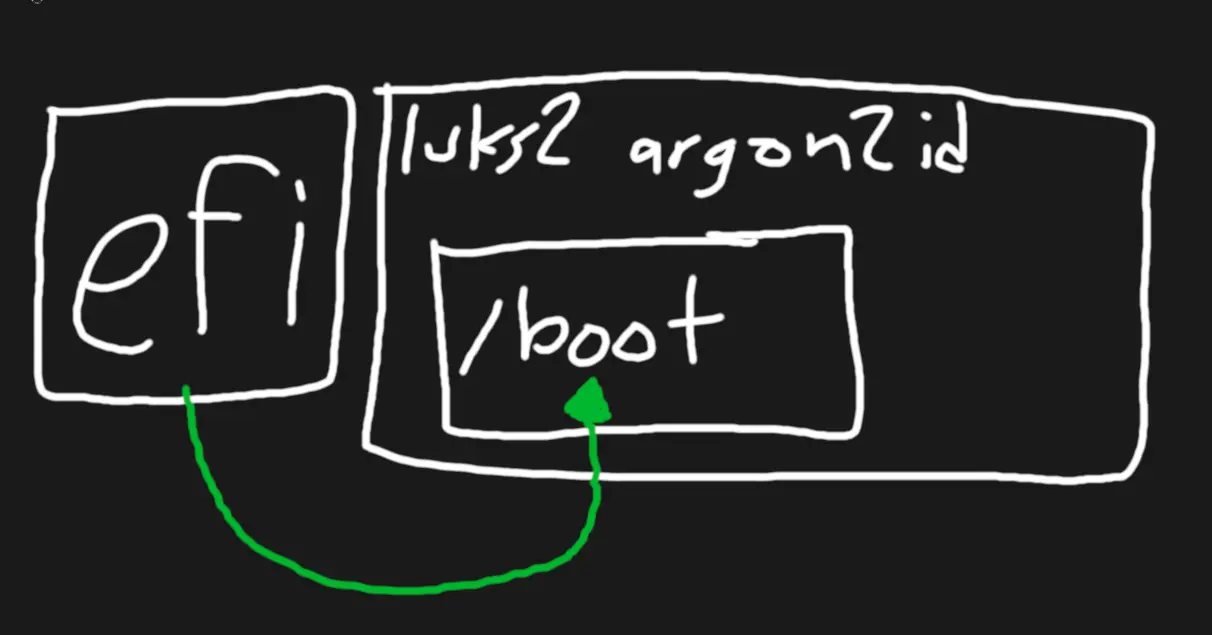
When you cryptsetup luksFormat, LUKS2 cryptography defaults to argon2id, a competition-winning gpu-resistant multi-core memory-hard algorithm thingy. Only problem is everyone only supports pbkdf2 instead :3
- GRUB had an argon2id support patch in the works. Buuut it stopped because a version-pinned dependency added argon2id support, and GRUB wants to update lib x to update lib y to update lib z to update said dependency (2 years later... I'm here D: )
- systemd-boot is simple and doesn't support argon2id
- efistub, i.e. making the kernel boot itself (i think?), necessitates secure boot and I'm not sure that's the best way to do this (Ventoy can bypass secure boot with MOKMANAGER funkin' anyway, can't it?)
- Raspberry Pi's bootloader might support argon2id? idk
Not to be deterred, I tried manually patching GRUB (tried with aur on a usb, then with portage) but I don't think these are supported with the latest GRUB. (Attempted with whatever the aur package uses, then Gentoo's grub-2.12-r4, then Gentoo's grub-2.12-r5, then git cloning and checking out older versions manually, then picking the earliest 2.12 archive.org tarball to patch lol. All failed with "couldn't find disk"-esque issues)
Does anyone have this working at or after Nov 2024? And better yet, am I missing something obvious ¯\_(ᵕ—ᴗ—)_/¯
Threat model: Avoiding a twopointfouristan prank, but also just screwing around for fun (◡‿◡✿)
Well thats only slightly terrifying. I thought tpm was the fix to this since it will verify the boot itself but thats doesnt seem to be available for most systems.
TPM can be the fix, but it needs to be integrated into the boot process correctly.
https://0pointer.net/blog/brave-new-trusted-boot-world.html mentions some or most of the pitfalls
Hmm would anyone know how to do it properly with qubes on framework?
TPM's can leak keys, with hardware access