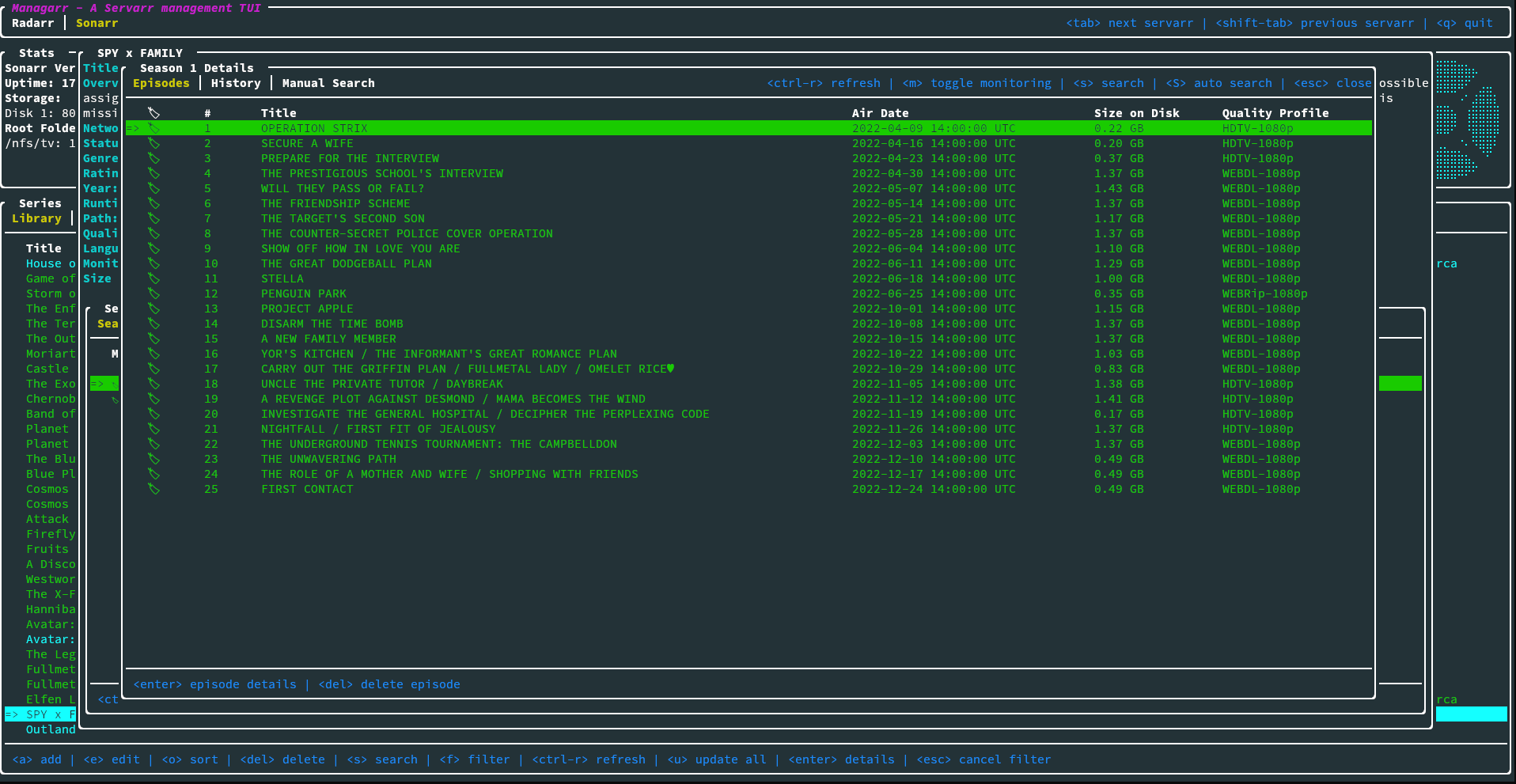
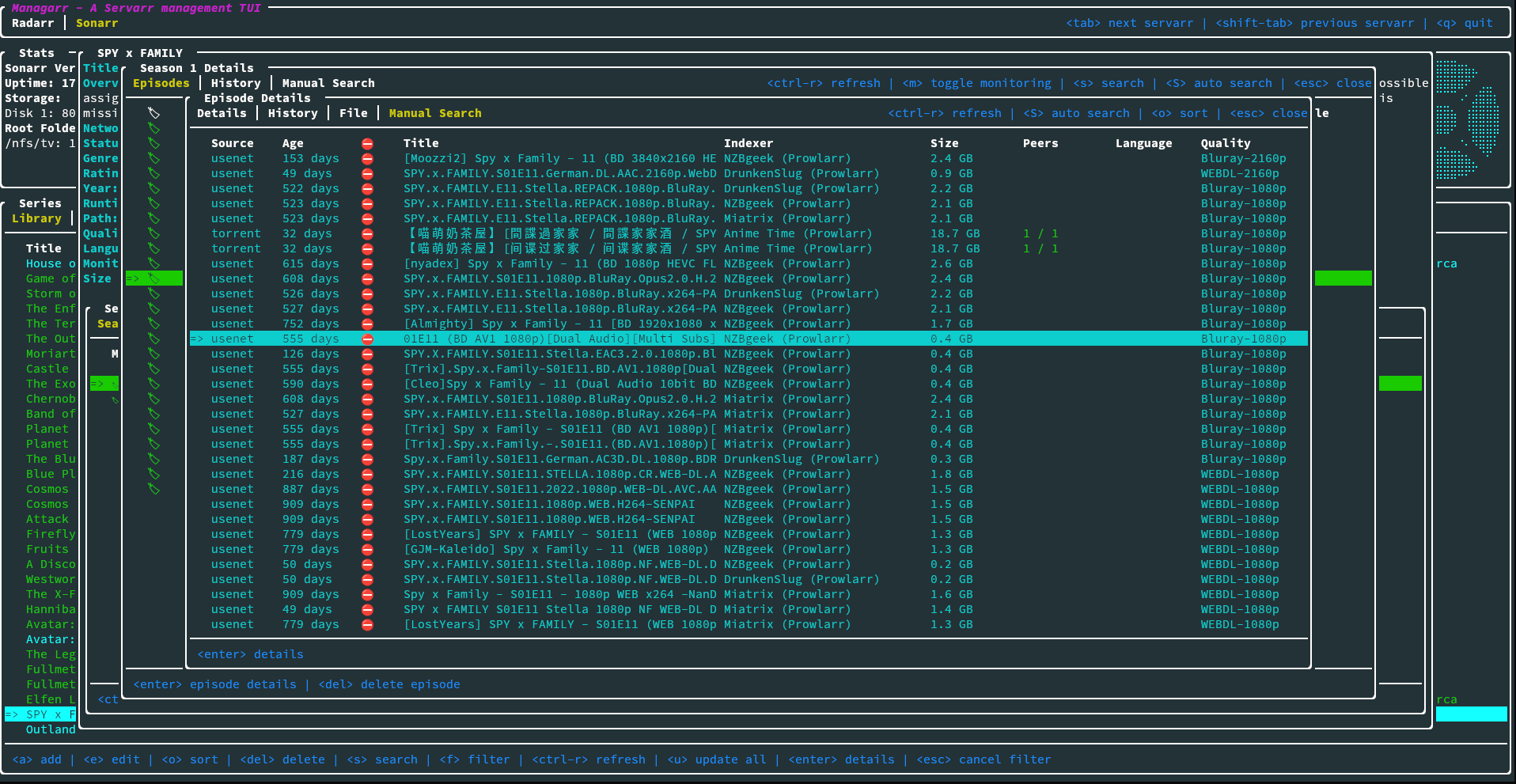
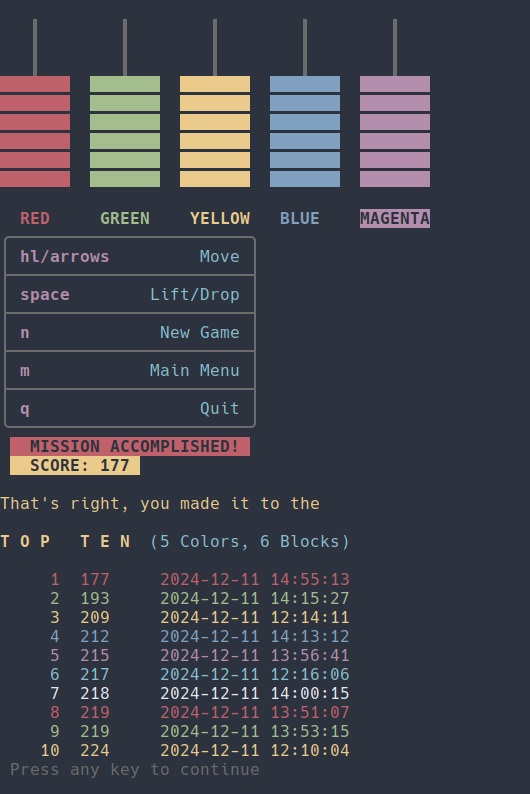
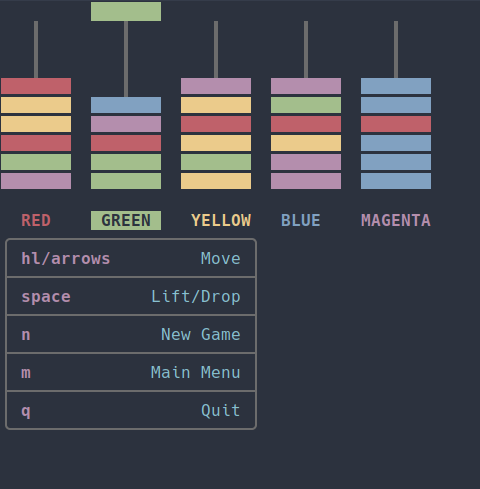
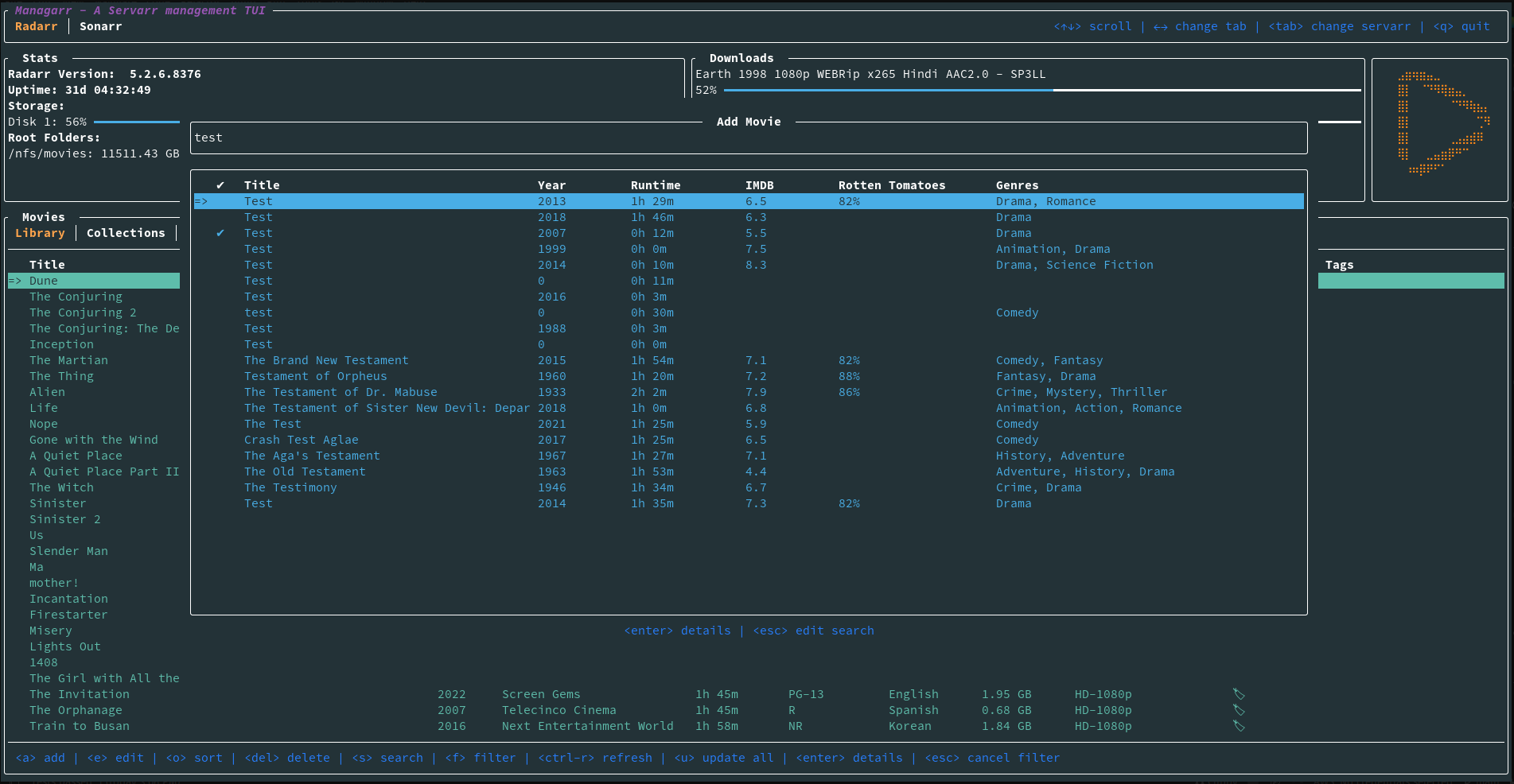
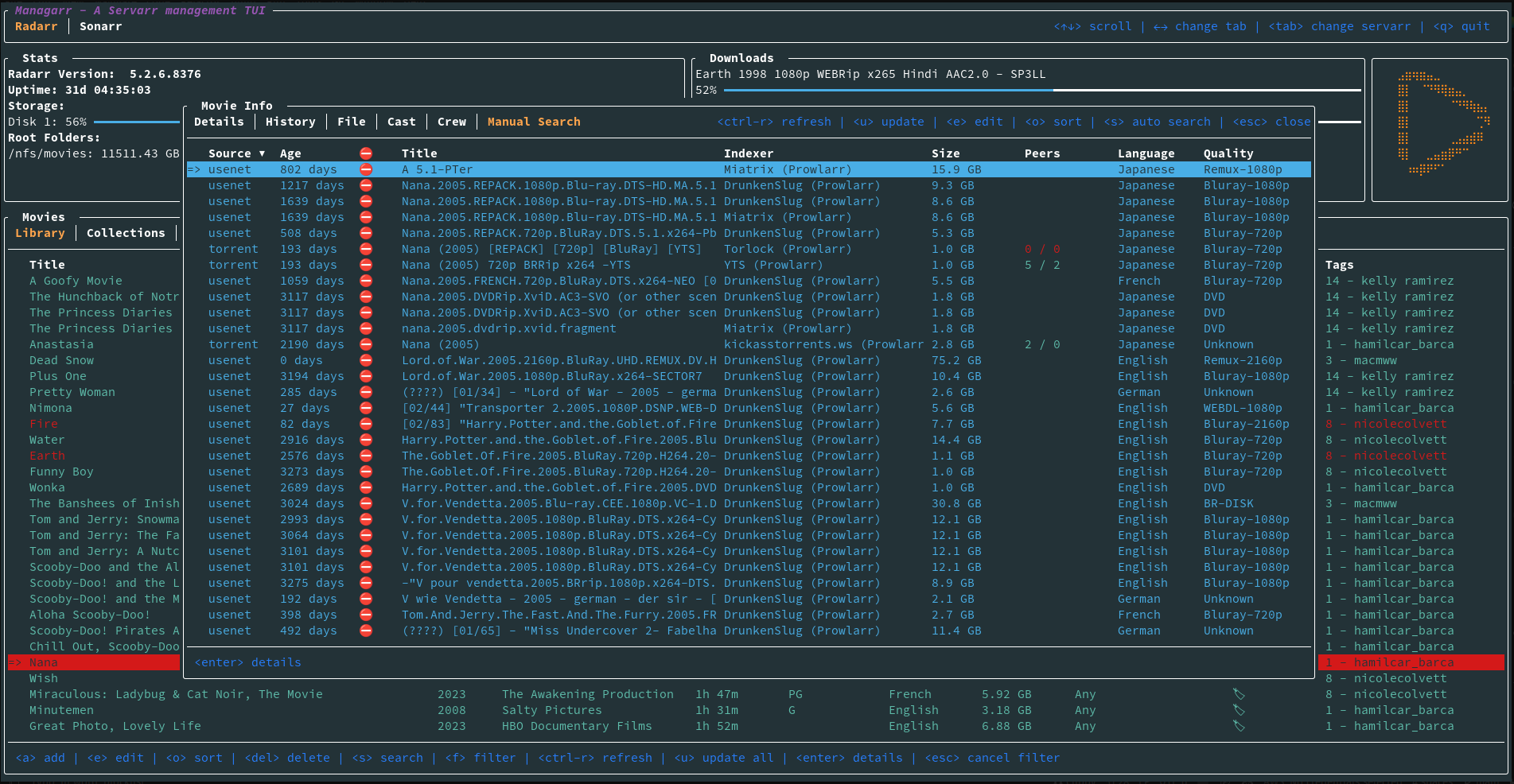
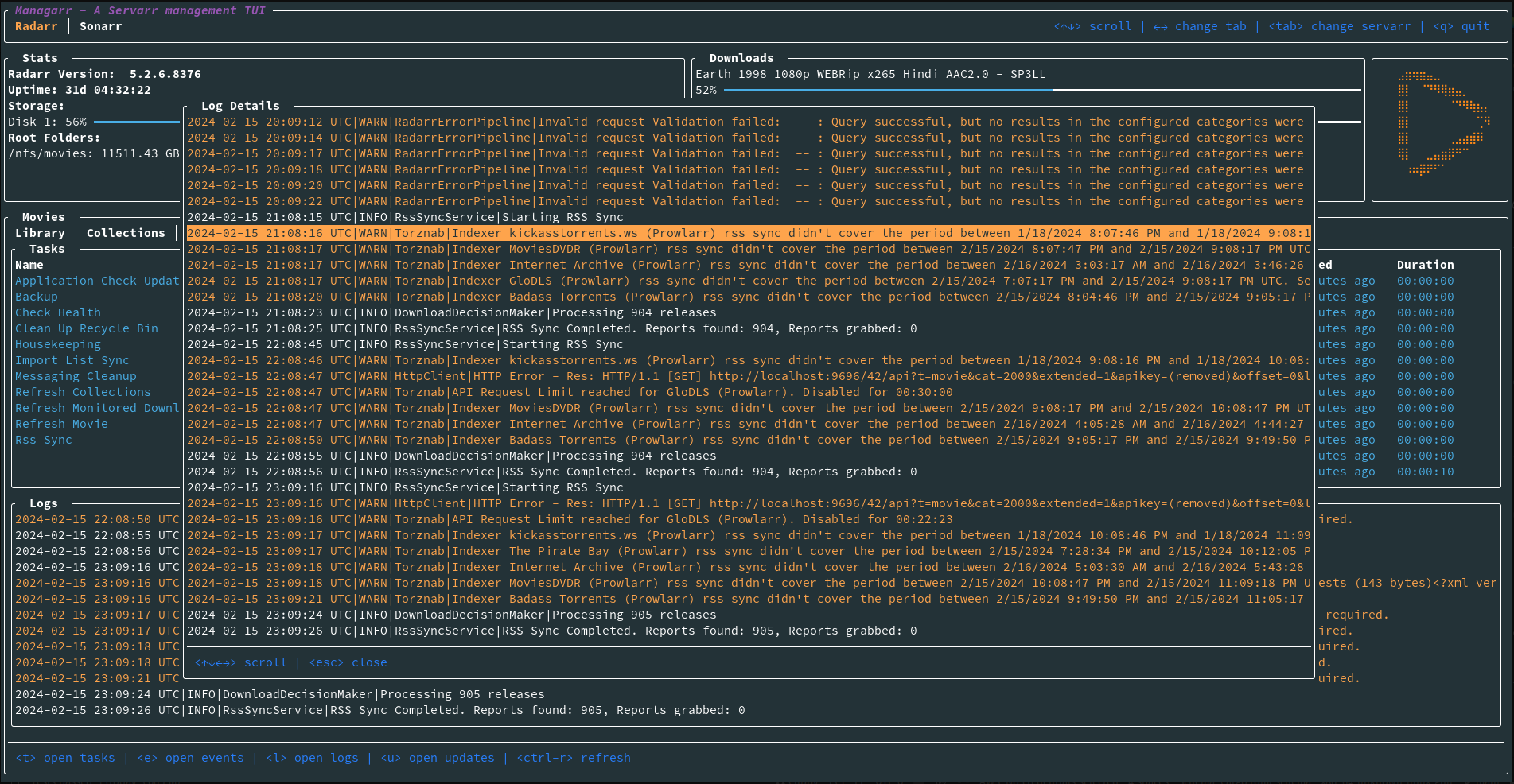
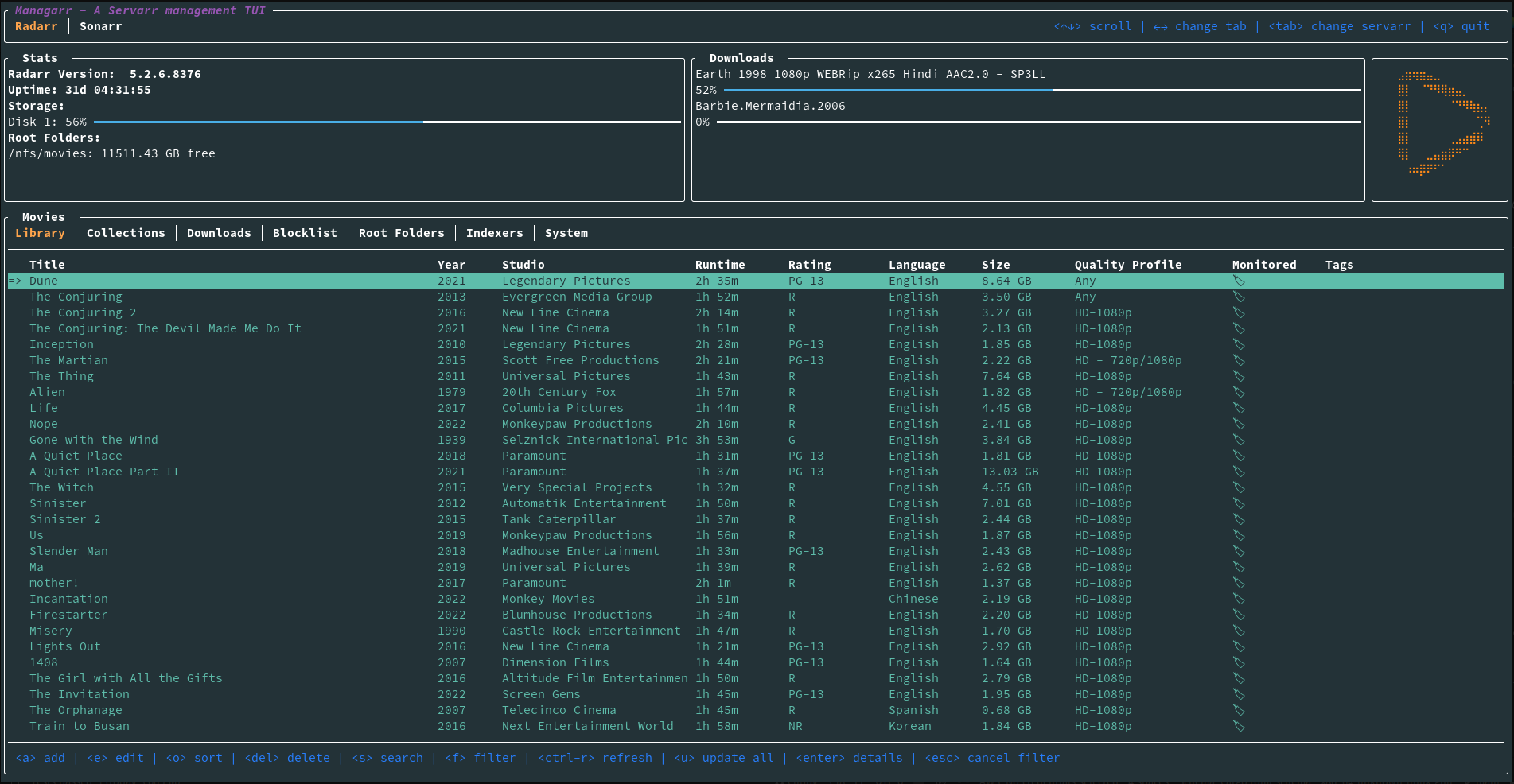
commandline
1963 readers
1 users here now
founded 2 years ago
MODERATORS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
24
25
view more: next ›