Gotta support open source wherever you can.
linuxmemes
I use Arch btw
Sister communities:
- LemmyMemes: Memes
- LemmyShitpost: Anything and everything goes.
- RISA: Star Trek memes and shitposts
Community rules
- Follow the site-wide rules and code of conduct
- Be civil
- Post Linux-related content
- No recent reposts
Please report posts and comments that break these rules!
Genetic diversity protects a species against epidemic disease
that's why i support flatpak as the universal package manager, vírus can't work there
That sounds like a challenge!
actually good idea lmao
Attacker will steal your browser cookie the same way it does without flatpak. If you have poor security hygiene and bad habits, flatpak nor anything else will save you.
if yoy fuck over with the default package manager, the attacker has your system, if you fuck over with flatpak, they have your browser cookie, my point still stand
sure, nothing beats good security hygiene and habits, but another security layer(plus others flatpak benefits) are a good thing
What you are describing here is fase feeling of security. Many flatpaks have access to your home dir by default. This is already security flushed down the toilet. Browser is the biggest attack vector nowadays and this is where your accounts reside. Worrying about package manager while not giving a shit sbout bank account seems out of place.
I can break my install just fine without any outside help thank you much and please 🤣😂😭
I wish someone would send me $5 out of pity for my non-malware code.
Sure, send me your github username and your ko-fi link and I'll judge you accordingly
Like the good old Albanian virus
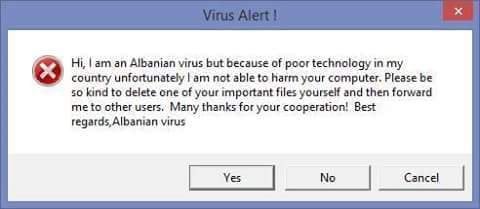
I feel personally attacked. Yes I've actually done this (minus sending them money). I had a server (that I am pretty sure sent headers to the effect that it ran x86) which had some logs indicating someone had tried to download an arm IOT botnet onto it. So I downloaded it and tried running it through a decompiler. I found a UPX stub. The rest was compressed. So I tried the UPX unpacker. This didn't work because it was built with a modified copy of UPX. So I hauled out a raspberry pi, reflashed the OS and tried running it in GDB in hopes of just dumping the unpacked bit from memory. Nothing. So I downloaded qemu and set up an aarch 64 arm 9 image still nothing. So I tried 32 bit arm again in qemu. At this point I gave up
cmalw-lib-2.0
The programer's version of lawful evil
That’s why you don’t write a virus for Linux…
This guys fucks
Pull requests welcome
This is pure gold.
Also true :)
