this post was submitted on 17 Jul 2023
13 points (88.2% liked)
Lemmy.world Support
3202 readers
2 users here now
Lemmy.world Support
Welcome to the official Lemmy.world Support community! Post your issues or questions about Lemmy.world here.
This community is for issues related to the Lemmy World instance only. For Lemmy software requests or bug reports, please go to the Lemmy github page.
This community is subject to the rules defined here for lemmy.world.
You can also DM https://lemmy.world/u/lwreport or email [email protected] (PGP Supported) if you need to reach our directly to the admin team.
Follow us for server news 🐘
Outages 🔥
https://status.lemmy.world

founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments


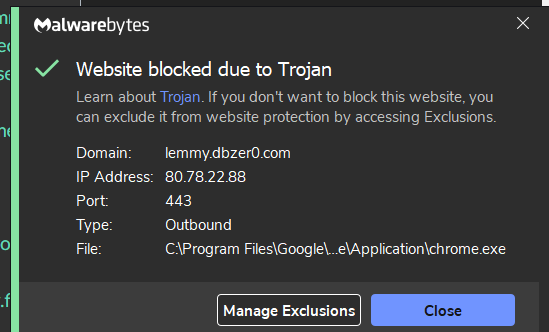
VirusTotal doesn't show any infections for that url.
I've seen a few false positives with BitDefender for random Lemmy instances too. It might be the heuristics being triggered by the random URL names, but it's also possible there were random exploits like the XSS vulnerability that were caught by some antivirus apps. Considering Lemmy is still a juicy target for bad actors, some precaution is probably warranted.
In general I'd look closely at the specific detection to make sure it's not flagging a suspicious JS file, etc.
Its a IP hit, not DNS
https://www.virustotal.com/gui/ip-address/80.78.22.88/community
Because the site is behind a login, you would have to upload the JS files individually to virustotal. However, there are no trojans that can affect you from visiting a website. Browsers have sanboxing to prevent that. What web threats usually do is steal keystrokes, serve ads, phish banking sites etc. To get infected by a trojan you would have to download a file and execute it.
Actually drive by JS attacks and JavaScript engine exploits happen occasionally and have known to bypass browser sandboxes. In these cases the infection is completely invisible to the user and requires no downloads or execution of files.
Yeah you're right. But browser zero days are usually targeted attacks not casting a large net like the usual web threat. Thanks for the link, it was interesting to learn some more techniques that are used in developing those. In this case the threat detected was Go based ransomware.
The
Trojanmention is worrying, though. Does it provide any more details about what it's flagging?