this post was submitted on 21 Aug 2024
694 points (97.5% liked)
Curated Tumblr
3855 readers
85 users here now
For preserving the least toxic and most culturally relevant Tumblr heritage posts.
Image descriptions and plain text captions of written content are expected of all screenshots. Here are some image text extractors (I looked these up quick and will gladly take FOSS recommendations):
-web
-iOS
Please begin copied raw text posts (lacking a screenshot that makes it apparent it is from Tumblr) with:
# This has been reposted here to Lemmy as part of the "Curated Tumblr Project."
I made the icon using multiple creative commons svg resources, the banner is this.
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
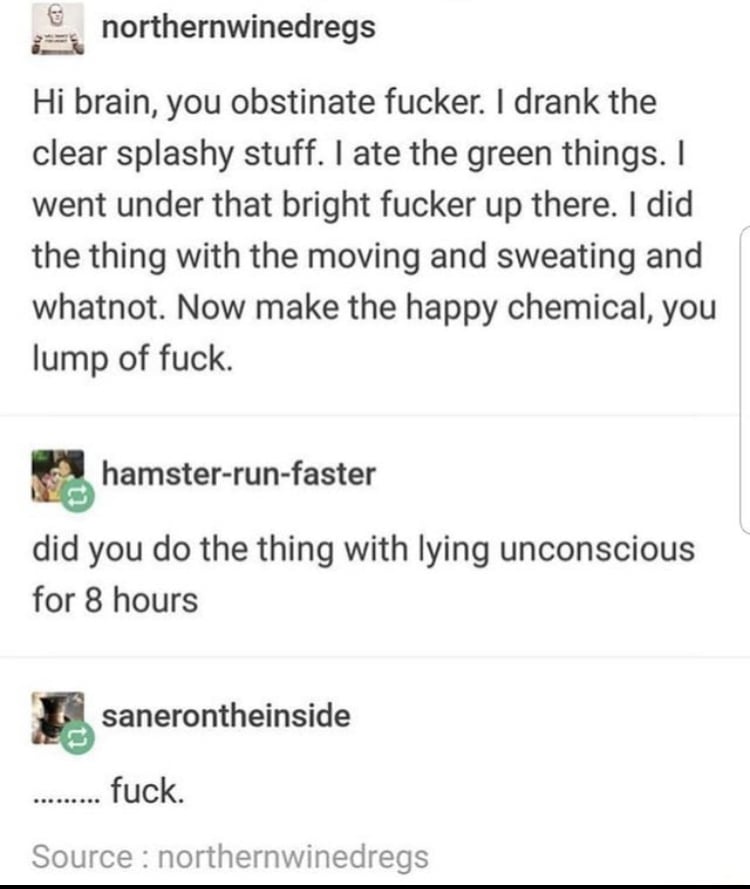
AutoHotkey is a good way to just have your mouse move a bit every 2 mins.
FYI I work in cybersec and if your company uses any sort of EDR like Crowdstrike on the company machine we can easily search for and find AHK running if there's cause. We don't search things unless there's a sec alert, but there are tons of false positives. I wouldn't report it if I saw but YMMV. Policies also vary.
Much better to use a hardware jiggler. I think the Flipper Zero has an app for it that makes it work over Bluetooth.
Can a powershell script get caught?
Yeah easily could be if someone looked.
Generally it's a safe assumption that your employer machine is fully compromised by them at ring-0 level, meaning they can see anything and everything from your browser history to your RAM, though the features of Crowdstrike specifically are fairly limited in that regard.
Now whether it will trigger an alert by itself or not depends.
Crowdstrike will often fire events for unrecognised scripts that match some heuristics, e.g. on Unix likes a lot of input redirects (pipe or >) or scripts over certain char length seemingly tend to be picked up.
We often get false positives from various IDEs using long tool chains on a CLI under the hood when compiling programs on dev machines for instance. System shells (bash, ksh, zsh, powrshell, cmd.exe) tend to produce more false positives than e.g. something like Python, so I assume they have much more aggressive detection.
In that case AHK is probably better as long as it's possible to install.
I wouldn't worry too much about being caught. Most cybersec teams and IT are so stretched and we're not narcs on average.
Just keep in mind that if you do this you should be able to afford losing the job in extremely unlucky circumstances.