When you cryptsetup luksFormat, LUKS2 cryptography defaults to argon2id, a competition-winning gpu-resistant multi-core memory-hard algorithm thingy. Only problem is everyone only supports pbkdf2 instead :3
- GRUB had an argon2id support patch in the works. Buuut it stopped because a version-pinned dependency added argon2id support, and GRUB wants to update lib x to update lib y to update lib z to update said dependency (2 years later... I'm here D: )
- systemd-boot is simple and doesn't support argon2id
- efistub, i.e. making the kernel boot itself (i think?), necessitates secure boot and I'm not sure that's the best way to do this (Ventoy can bypass secure boot with MOKMANAGER funkin' anyway, can't it?)
- Raspberry Pi's bootloader might support argon2id? idk
Not to be deterred, I tried manually patching GRUB (tried with aur on a usb, then with portage) but I don't think these are supported with the latest GRUB. (Attempted with whatever the aur package uses, then Gentoo's grub-2.12-r4, then Gentoo's grub-2.12-r5, then git cloning and checking out older versions manually, then picking the earliest 2.12 archive.org tarball to patch lol. All failed with "couldn't find disk"-esque issues)
Does anyone have this working at or after Nov 2024? And better yet, am I missing something obvious ¯\_(ᵕ—ᴗ—)_/¯
Threat model: Avoiding a twopointfouristan prank, but also just screwing around for fun (◡‿◡✿)
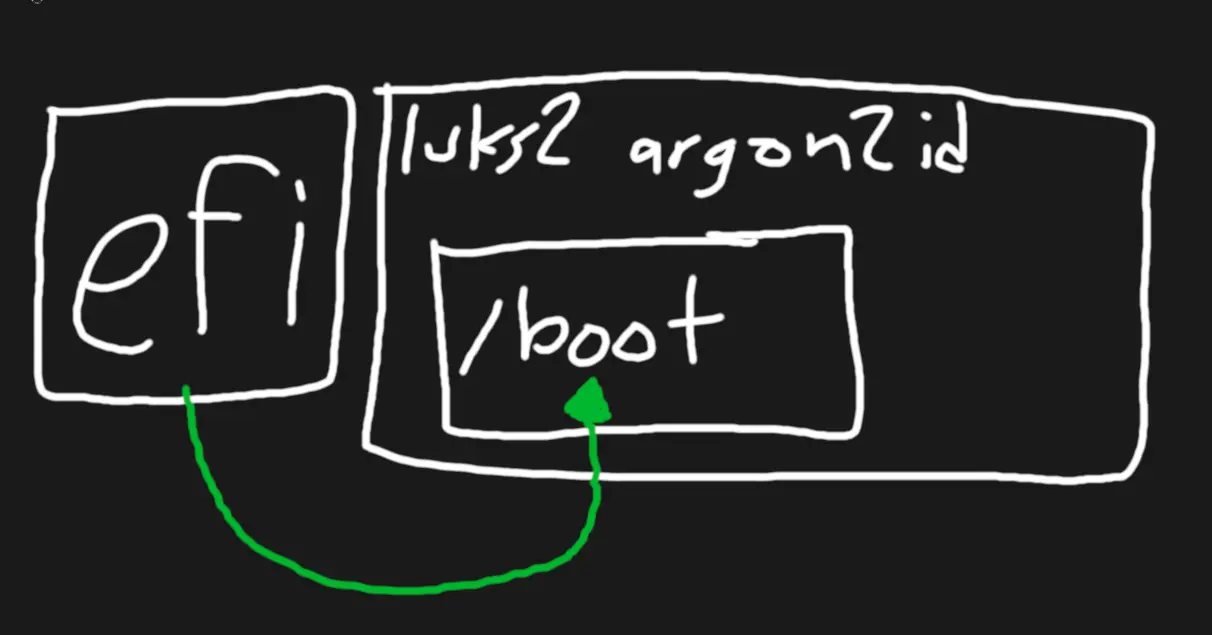
Please let me know if you figure it out. I opted the detached header approach a few years ago because it had most of the same benefits without the headache and poor support. I'm wondering if it might be possible to replicate what Grub is doing as it us relatively trivial but that doesn't mean easy. Basically you'd have a Secure Boot signed bootloader that is able to boot a protected file system (secondary /boot) where your kernel & initramfs, or combined image exists. This secondary boot partition can be a lot more flexible though so it could even read a sparse-baded file that has a file system stored in it, and then from there you'd unlock the second layer of encryption. My guess is it can be done using something besides Grub and you'd have full access to all the algorithms available under cryptsetup.